| Active |
|---|
| This application does not need additional settings. So you can make connectionUnique, active service acces point to a network. There are different types of connections (API key, Oauth…). More only by using your login credentials or by following the instructions below . |
The SSH moduleThe module is an application or tool within the Boost.space system. The entire system is built on this concept of modularity. (module - Contacts) More allows you to execute commands on a remote server.
Boost.spaceCentralization and synchronization platform, where you can organize and manage your data. More IntegratorPart of the Boost.space system, where you can create your connections and automate your processes. More will connect to your SSH server from its IP addresses. Ensure you whitelist these IPs to allow connections to your remote server.
To connect SSH:
-
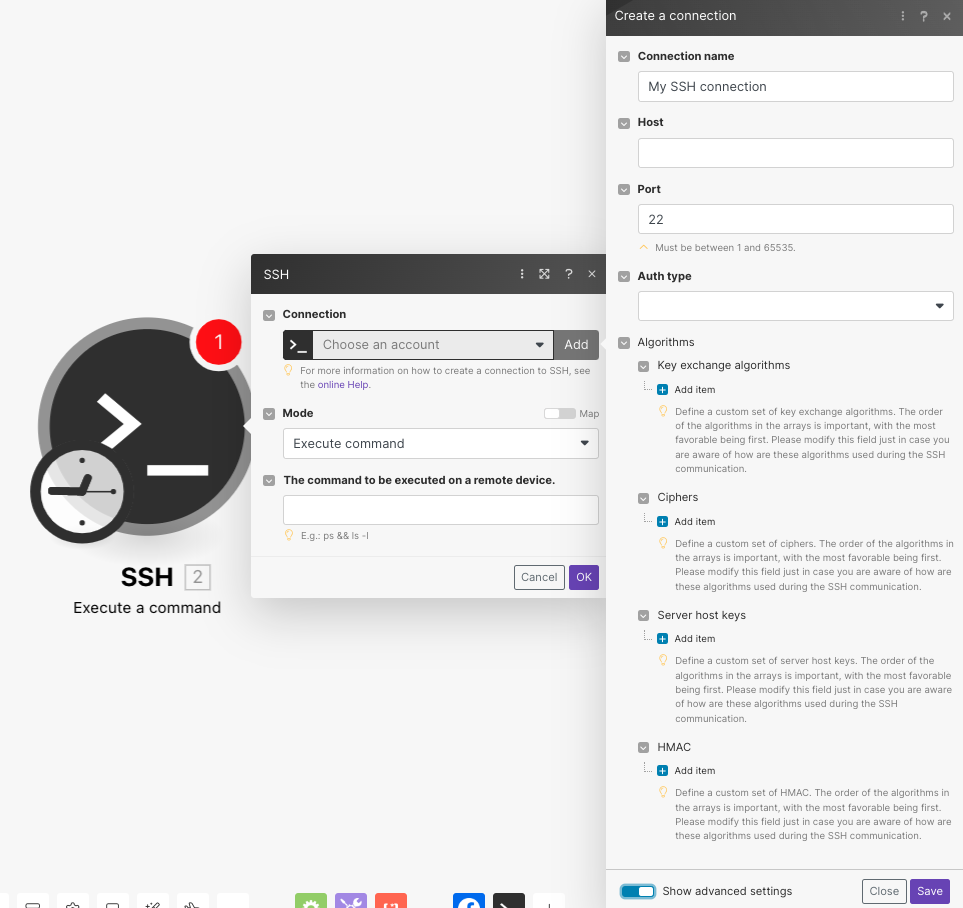
Log in to your Boost.space Integrator account, add an SSH module to scenarioA specific connection between applications in which data can be transferred. Two types of scenarios: active/inactive. More, and click the Add button next to the Connection field.
-
Enter the details as given in the table as a reference.
Connection name
Optional: A name for the connection.
Host
Enter the host address of the server you want to connect.
Port
Enter the number of the port you want to connect to. Must be a number between 1 and 65535. The default is 22.
Auth Type
Select the authentication type and add the details:
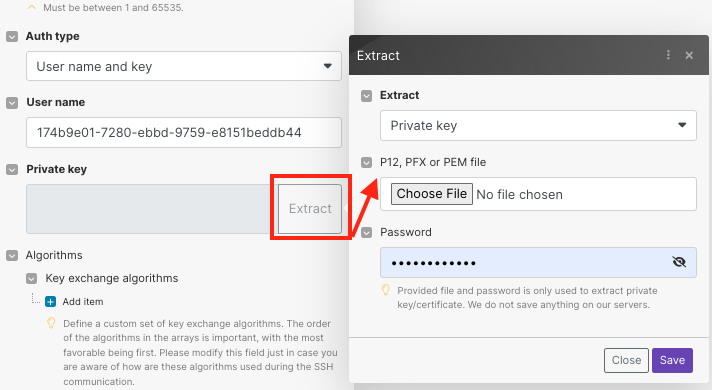
You can click Extract and upload the Private Key and Certificate file. The supported files are P12, PFX, or PEM.
Algorithms
Add the optional algorithms:
-
Key exchange algorithms – Define a custom set of key exchange algorithms. The order of the algorithms in the arrays is important, with the most favorable being first. Please modify this field just in case you know how these algorithms are used during SSH communication.
-
Ciphers – Define a custom set of ciphers. The order of the algorithms in the arrays is important, with the most favorable being first. Please modify this field just in case you know how these algorithms are used during SSH communication.
-
Server host keys – Define a custom set of server host keys. The order of the algorithms in the arrays is important, with the most favorable being first.
![[Note]](https://docs.boost.space/wp-content/themes/bsdocs/docs-parser/HTML/css/image/note.png)
Note Modify this field only if you know how these algorithms are used during SSH communication.
-
HMAC – Define a custom set of HMAC. The order of the algorithms in the arrays is important, with the most favorable being first. Modify this field just in case you know how these algorithms are used during SSH communication.
-
-
Click Save.